Amazon Prime Day 2022 is Coming: Here are Quick Cybersecurity Tips to Help You Stay Safe
Amazon Prime Days this year are July 12 – 13th, 2022. As a result, cybercriminals are taking every step to capitalize on the holiday with new phishing attacks. I have been getting asked about common types of Amazon-related scams and wanted to share what to look out for.
1. What are some of the most common/popular Amazon-related scams (Amazon impersonators, other criminal actors or scams??)?
Phishing emails using the Amazon brand to add legitimacy top the list, but scams involving text messages and even phone calls saying they are from Amazon have been reported. These scams use the fact that just because of the huge numbers of customers that Amazon has, the odds are in the scammers favor that if they send an attack using Amazon as the source, they will get to someone with an account. Many of these scams are designed to steal the login credentials from users by sending them to a fake login screen that steals the username and password. Once they have access to the account, it is a simple task to make purchases with credit card information saved in the account. From purchasing physical goods that can be delivered the same day to buying virtual gift cards that can be resold or used before the scam is uncovered, the opportunity to steal money or merchandise is huge. Once credentials are stolen, scammers will often immediately change the password, keeping the legitimate account owner locked out of the account and buying them time to make purchases. The advanced tracking that many Amazon packages have, where they can show you the location of your delivery on a live map, are also a great way for scammers to quickly intercept the package as it is delivered, even giving them an opportunity to wait outside for the driver to hand them the package.
2. What should users be on the lookout for?
Notices about account problems or delivery problems will always be found within the account when a person logs in to Amazon’s website. Rather than following a link in an email, it is safer to log directly into the Amazon website to resolve any issues they may have. Scams such as these often use scare tactics to get people to rush through a process without thinking clearly. Anytime a person receives an email, phone call or text message that elicits a strong emotional response, they should take a deep breath and treat it suspiciously. In addition, consumers can help protect their accounts by enabling multi-factor authentication on their accounts, this will require a code that will be sent in a text message or generated in a smart phone app, in addition to the password, to log in to the account. Although not perfect, this can help in the event the scammer guesses your password or steals it.
3. What should a user do if they face one of these Amazon scams?
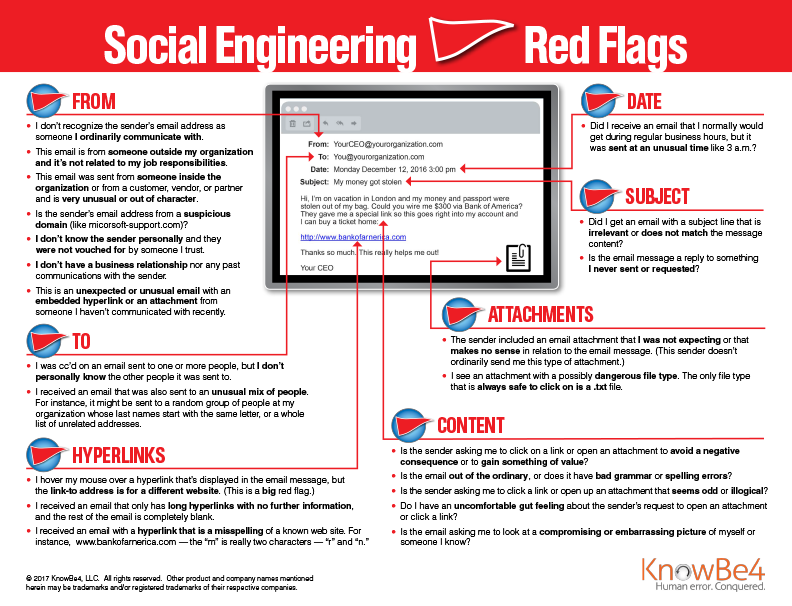
If it’s an email or text message, simply deleting it is the wisest course. If it’s a phone call, simply tell them that you will go to the website and look into whatever the issue is. You can also tell them you will call the customer service number from the website directly, and ask for their extension and name. Any legitimate caller from Amazon’s customer service department will understand. Be aware that the scammers will be pushy, however safety comes from remaining calm and thinking critically. Here is a helpful one-sheet to help your users remember some common red flags of social engineering scams, get the full PDF here.
Source: https://blog.knowbe4.com/amazon-prime-day-cybersecurity-tips



