identify, analyze, and respond to cyber threats
MDR is a Threat Detection service that provides an organization with the tools to effectively identify, analyze, and respond to cyber threats before they disrupt the business. Threat Detection and response is a solution to many of the challenges faced by enterprises endeavoring to improve cybersecurity maturity. Organizations have multiple traditional security controls at their disposal. However, these controls are not appropriately integrated to elicit any actionable intelligence. Threat Detection integrates security capabilities with threat insights to help monitor, detect, and respond to evolving threats.
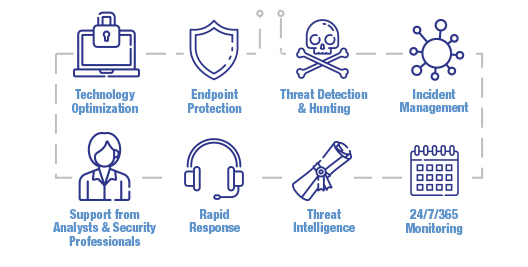
Rather than being a preventative measure, our IT360 Threat Detection Service gives you a plan of action to prevent, detect and remove malicious threats. Threat detection isn’t just another automated tool – our human security engineers are tasked with one-to-one threat analysis and remediation. With this added human touch, Threat Detection becomes much more than just another cyber security solution and puts some of the sharpest technical minds in your security driving seat.
Our ThreatOps team actively investigates any new potential threats uncovered by our software, exploring each vulnerability in detail. Custom incident reports are created and sent to you for every vulnerability found, providing information about the threat and simple removal steps.
Considering a Change?
Are you considering a change in IT providers, but concerned with the effort it will take to do so? It may not be as difficult as you think…


