New data shows an upswell of email-based cyberattacks, with over 256 brands being impersonated, as social media, Microsoft, shipping, and ecommerce brands top the list.
There’s been a lot of changes in the volume of email-based cyberattacks, according to security analysts at Abnormal Security. According to their H2 2022 Email Threat Report, the number of attacks per 1,000 mailboxes has increased over the last 12 months by nearly 50%. And if you take into consideration the all-time low in January of this year, the number of email-based attacks just six months later are nearly 4 times as much as at the beginning of 2022.

The overwhelming majority (68%) of email-based attacks were phishing attacks. Most of these attacks were targeting credentials using the impersonation of well-known brands. According to the report, nearly one-third (32%) impersonated a social network (LinkedIn was the top brand impersonated – something corroborated by a recent report from Checkpoint). One-fifth of phishing attacks impersonated Microsoft. In both cases, the predominant attack trait was an intent to steal the victim’s credentials to that platform.
The emails are well-written and look official. Here’s an example of one impersonating LinkedIn:
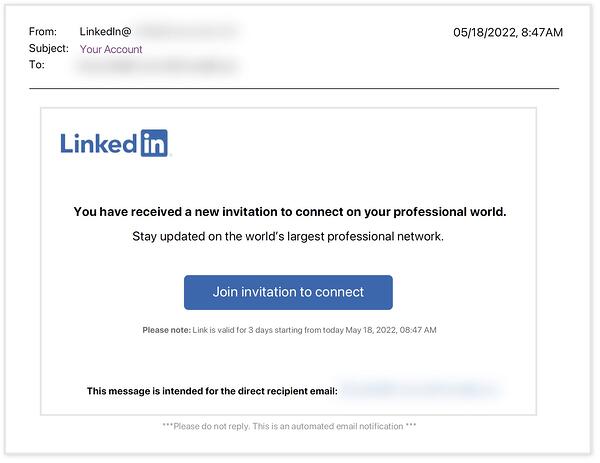
And another impersonating Microsoft:

Over 256 individual brands were impersonated – including financial services, ecommerce, business management, infosec, travel, telecom, and more. The goal is to obtain viable credentials that can be used to launch additional campaigns from a legitimate email account, access bank accounts, sell on the dark web for access to a corporate network, and more.
Phishing attacks are the root of the problem and require a layered solution that includes conditioning your users to remain vigilant each and every time they interact with an email – something taught through continual Security Awareness Training. The sooner users default to assuming any email that seems suspicious or unexpected is considered malicious until proven otherwise, the better for organizations today.
Source: KnowBe4


