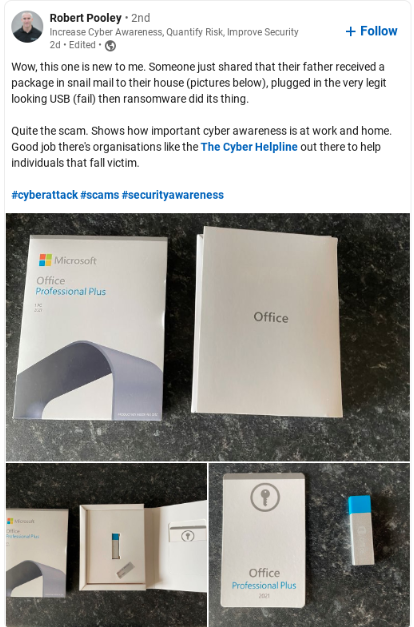
Just when you thought scammers couldn’t get more tricky in their attacks, this example will prove you wrong. One of our KnowBe4 colleagues shared this LinkedIn post on a recent very crafty USB scam:
As you can see, the Microsoft USB looks VERY similar to a USB you would receive from Microsoft in the mail as part of an Office Professional Plus delivery. Unfortunately, the USB was plugged into the victim’s computer and ransomware infected the machine.
This should be a valuable lesson for anyone that receives something in the mail that is software – ALWAYS assume that it could be malicious and always double-check with your organization to ensure that it is safe. New-school security awareness training helps your users identify common red flags. New-school security awareness training can help your users identify the common red flags.
And here is a new blog post by Roger Grimes that digs deeper into this malicious USB problem:
https://blog.knowbe4.com/beware-of-sophisticated-malicious-usb-keys.
Source: KnowBe4


